

Virtualization
The advent of virtualization technology revolutionized the way hardware could be used in many different businesses. Virtualization of applications and desktops has allowed easier access to users and employees, making remote work increasingly possible, and the virtualization of networks, storage, and servers improved efficiency and performance metrics for organizations in need of powerful and reliable infrastructure.
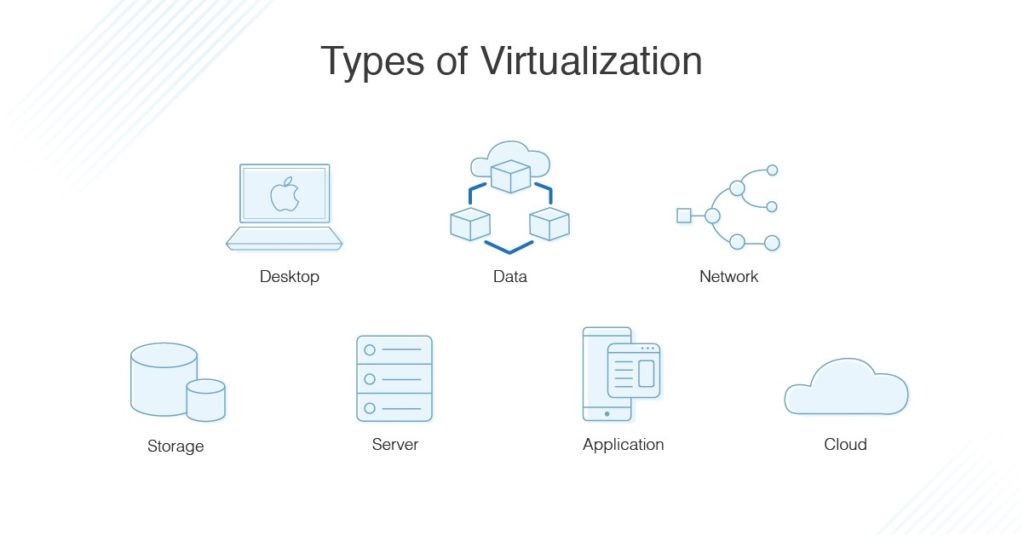
There are numerous different types of virtualization, and it’s important to understand cloud virtualization is simply one type of virtualization technology. Cloud computing isn’t different from virtualization, but it uses virtualization to function. Before we get to cloud virtualization, the other kinds of virtualization are:
There are several reasons virtualization of one of the above types is increasingly used, as there are numerous benefits. For example, in the case of server, storage, desktop, and application virtualization, having physical devices or copies of these things can be difficult to move or copy when you need to move something. A virtual server or desktop can be easily moved and accessed from a different location.
In addition, physical devices are limited by the specific set of hardware they’re installed on, while virtual devices can easily be allocated resources as necessary. Physical hardware can be consolidated, and a virtual machine could access resources from multiple pieces of hardware.
Furthermore, the level of isolation of virtual devices provides two main benefits: security and resistance to change. When a virtual machine is created, it’s completely isolated from other virtual machines and from the host system. If one virtual machine or one physical device is infected with malware, it won’t necessarily be able to easily spread through other virtual machines or other parts of the network. This level of security is useful for protecting your network when virtual machines access the internet and for testing applications or new developments. For example, if an application crashes on a virtual machine, it won’t cause any problems for the host machine beneath it.